It’s something we often see claimed (usually by companies with a shiny new product to sell), that shared hosting isn’t secure, and the question we get asked is, Is shared hosting secure?.
We’re going to take a look at what people are really asking, look at what a typical WordPress hack looks like and what you can do to make sure the hosting you’re using is secure. So if you’re interested in shared hosting security, read on.
What do “you” mean by secure?
The question of What is secure? is going to have different answers to different people depending on their circumstances and data. If you’re a bank then your definition of secure is going to be different to that of Aunt Mabel who runs the Cute Kitten Appreciation Society.
Of course there’s going to be a base level of security, as no one wants their visitors subjected to objectionable content etc. but the level of protection you need to be secure against a likely attacker is different.
The question you really want to know the answer to then is, Is shared hosting secure enough for my website and use?, let’s take a look.
Shared hosting has come a long long way
Don’t believe the hype, shared hosting (we call it virtual hosting) isn’t inherently insecure like some people such as WPMU DEV would have you believe, who described it as:
…insecure, slow…
Sure, if you were running the same setup in 2022 as you were in 2002 then it would be insecure and slow, but who would do that? As it turns out, quite a few hosting providers based on our recent experiences of migrating sites for our clients.
We recently moved a series of sites for a client from a once popular palindromically named host over to their hosting with us and within seconds our security systems were lighting up like a Christmas tree. Just for transparency, we should make it clear that the sites were migrated on to the agency’s own server – but the server was set up and configured in the same way, with the same software, security etc. as our own shared/virtual hosting.
For an extra bit of transparency, that quote from WPMU DEV came from their page where they are trying to sell their own hosting solution.
What does a hack look like?
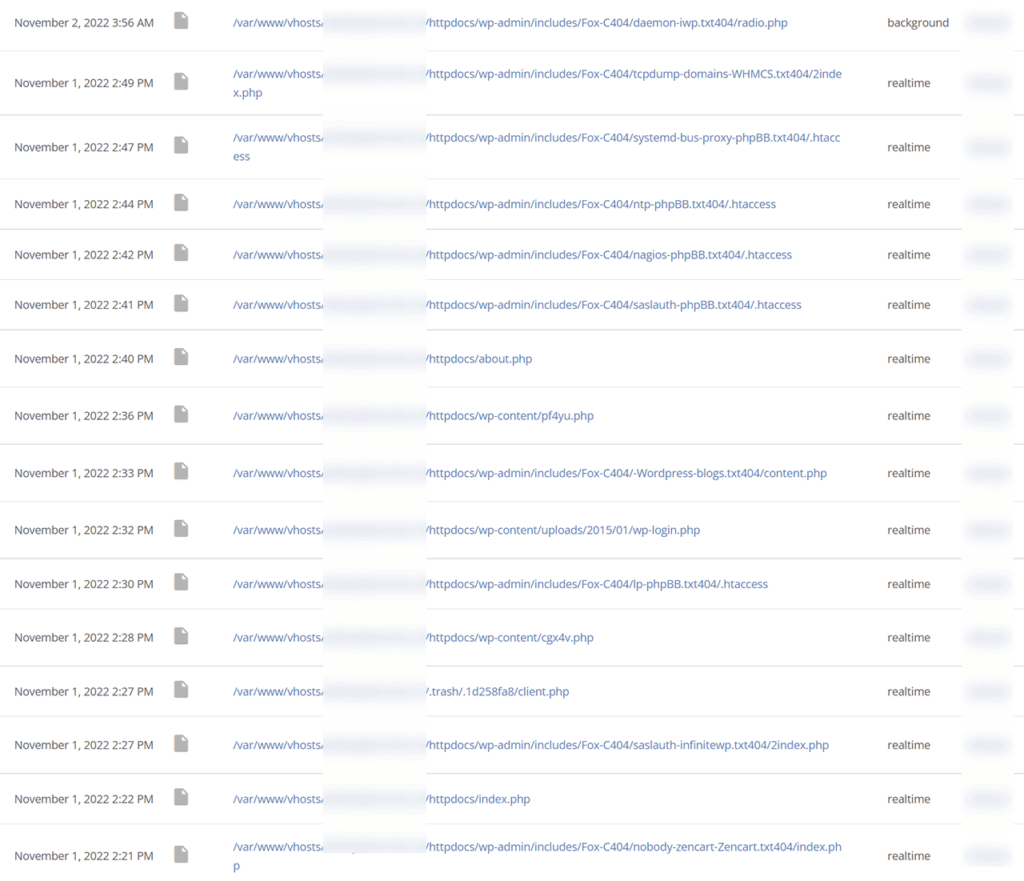
For the WordPress sites this agency client were taking over it looked exactly like this in our security software:
That’s just the tip of the iceberg though, there were pages and pages just like this for the 5 sites we migrated, a mixture of backdoors/shells, malware distributors and other assorted “bad things” meaning that the hackers could read and write any files in the account, as well as the database.
Fortunately the fact they’ve shown up there means that the server has either cleaned or deleted the files in question (depending on if they are genuinely needed or not) having checked every file uploaded. We also check files when they are accessed again and also inside databases.
The WordPress Tool Kit in our control panel also detected and fixed several errors with the core WordPress files over and above malware.
Was this an isolated incident?
Unfortunately it’s not, but neither is it an issue specific to shared hosting as some would claim and have you believe.
We’ve seen the same issues with sites moved from cloud servers/VPS/cloud instances and from dedicated servers because they’ve been set up in the same way the provider would configure their shared hosting meaning all the same problems are present. The same issues will occur inside hosting based on containers as well, because the entry points for malware are usually a bug in the application code somewhere, not the underlying hosting platform itself – so if nothing is checking that code still, malware will get in.
It’s not just attacks from the internet
Of course it isn’t just attacks from the internet you have to think about with shared hosting, it’s also local attacks that originate on the server your website is on. Once an attacker can find a way to upload files to an account on the server they can become a local attacker – attacking your site and potentially others on the same server.
It’s not as bleak as it sounds
Fortunately once again, if things are configured correctly then the chances of a local attacker inside one customer’s account being able to damage yours are vastly reduced. There are some of the steps your host can take:
- Running all user supplied code as the user, not as a system wide username e.g. user1, user2 and not nobody, wwwuser etc.
- Setting correct permissions on files and directories to stop users seeing each other’s files
- or better still, creating a secure virtual filesystem for each user, that other user’s files don’t even appear in
- Isolating each user’s processes inside a security container (a bit like a virtual machine)
- Running live security updates against critical system software libraries
- Running live security patching of the operating system kernel
None of these will 100% eliminate the potential risks to your websites, as software is complex and there are always as yet undiscovered bugs, or even attacks against bugs in the hardware itself! It also comes down to what is secure enough for your use, and once again with the correct measures in place shared hosting can be secure enough for most uses.
What can you do to protect your sites?
Ask questions of any hosting company you’re going to work with. The first question should always be:
Is this service suitable for my intended use and the information I will be storing and processing?
After that, ask them what security they have in place:
- Does it try to prevent infections in the first place?
- Does it prevent malicious logins?
- Is it active or passive? Do you have to perform scans manually?
- Does it check inside databases?
- Does it clean up issues automatically or just block access to problematic files?
- Does it update critical software automatically?
- Does it isolate users from each other?
- Does it isolate users’ code from each other?
- Does it isolate users’ files from each other?
Any provider worth your business will answer these for you, if they try and claim they can’t tell you for security reasons then that’s a big red flag, security by obscurity isn’t security at all.
Some words of warning…
We aren’t claiming your WordPress website can’t be hacked on servers configured how we configure ours, because that’d just be silly, everything can be hacked by someone determined enough, but it does seem the way we do things is above and beyond what other providers do to keep your customers’ website’s safe from harm.
Be very wary of anyone claiming they can make your websites or server unhackable, that’s yet another big red flag.
We also recommend that if you find your WordPress or any website has been on such an insecure platform that it has many backdoors and issues, that you rebuild it from scratch as it can be very difficult to make sure you’ve removed all malware from files and inside databases.
So is shared hosting secure?
As with many things when it comes to hosting we hope you’ve realised the answer is, “it depends” and you need to ask questions. If you’re trying to protect against a determined adversary then it’s probably not going to be your first choice for hosting or if you’re storing health records or other very sensitive data.
If the service has been setup correctly and is being managed correctly then for the vast majority of websites it will be secure enough.
As always feel free to ask us any questions you may have, either by email, phone or the many social media channels we are on.